Increased reliance on the internet in Southeast Asia amid the COVID-19 situation has brought to the fore more vulnerabilities cybercriminals can exploit.
Increased reliance on the internet in Southeast Asia amid the COVID-19 situation has brought to the fore more vulnerabilities cybercriminals can exploit.
Cybersecurity company Kaspersky has announced a list of the top threats public and private organisations should watch out for.
Vitaly Kamluk, director of its global research and analysis team Asia Pacific, said: “The year 2020 is not like any other. This year is not only a time of changes, but it changed time itself. It changed the way we travel, the way we shop, the way we interact with each other. The computer threat model has evolved since COVID-19 started.”
At a virtual media conference with journalists in the region, he revealed how cybercriminals have added blackmail to their arsenal to ensure their victims would pay ransomware.
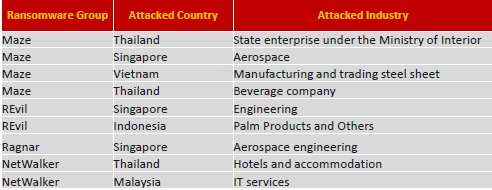
He confirmed the presence of top ransomware groups in the region targeting State, aerospace and engineering, steel sheet manufacturing and trading, beverage, and palm products companies, hotel and accommodation services and IT services firms.
Among the most notorious and earliest ransomware families is Maze. The group behind Maze ransomware has leaked victims’ data more than once after they refused to pay the ransom.
It has also created a website to reveal the identities of their victims and the details of the attack like date of infection, amount of data stolen and names of servers.
In January the group was involved in a lawsuit with a cable production company that resulted in the website being shut down.
The attack process being used by this group is simple. It will infiltrate the system, hunt for the most sensitive data and upload it to its cloud storage. The data is then encrypted with RSA.
A ransom will be demanded based on the size of the company and volume of data stolen. The group will then publish the details on its blog and even give anonymous tips to journalists
“We are monitoring an uptick in Maze detections globally, even against a few companies in Southeast Asia, which means this trend is currently gaining momentum,” Kamluk said.
“While the public shaming part of the attack adds to the pressure of bowing to the demands of these cybercriminals, I strongly advise companies and organisations not to pay ransom and to involve law enforcement agencies and experts in such scenarios. Remember that it is also better to have your data backed up and cybersecurity defences in place to avoid falling victim.”
To remain protected against these threats, he said enterprises and organisations should make backups, simulate attacks, prepare action plans for disaster recovery, deploy sensors everywhere (monitor software activity on endpoints, record traffic, check hardware integrity), train their staff while they work remotely, and others. — VNS





